Create Clients
Clients can be created per application to support the required integration scenarios.
The overall concept is explained here.
azuma doa aims to simplify the creation of new clients (authorization flow / client credentials) in the dashboard. Therefore, all explanations are embedded in the relevant forms.
Example (authorization code with PKCE):
The authorization code flow is used to integrate all your frontends (including single page applications, mobile apps and normal web apps) with azuma doa.
Since this flow is considered the industry standard for frontend integration, there are many stable libraries available, that implement this flow. We strongly recommend the usage of such libraries instead of custom implementations (see listing in e.g. https://oauth.net/code/).
By default, we enforce the usage of authorization code with PKCE to further improve security.
Most libraries only require the following definitions:
- OpenID configuration URL:
- Authority:
- ClientId (as defined in your client)
- Scopes (all or a subset of the defined scopes of your client)
- RedirectUrl (must be from the list of defined valid redirect urls of your client)
Example of the required oidc-react definition (with local development urls):
<AuthProvider
authority="*authority*"
redirectUri="http://localhost:3005/auth"
clientId="..."
scope="openid"
autoSignIn={true}
onSignIn={(user) => {
...
}}
>
...
</AuthProvider>
Example form to create an authorization code client (with PKCE):
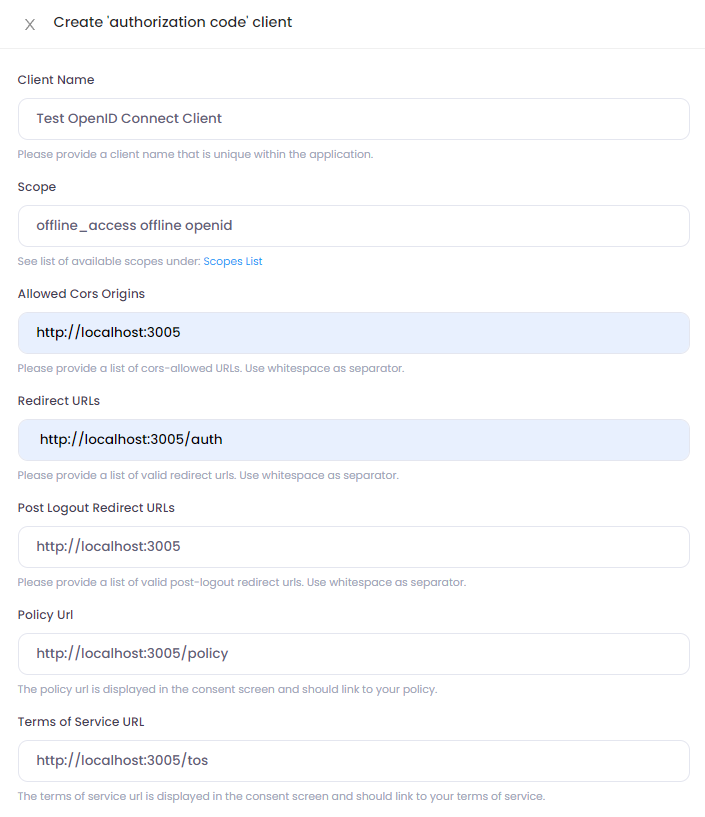
The following properties
Client NamePolicy UrlTerms of Service Url
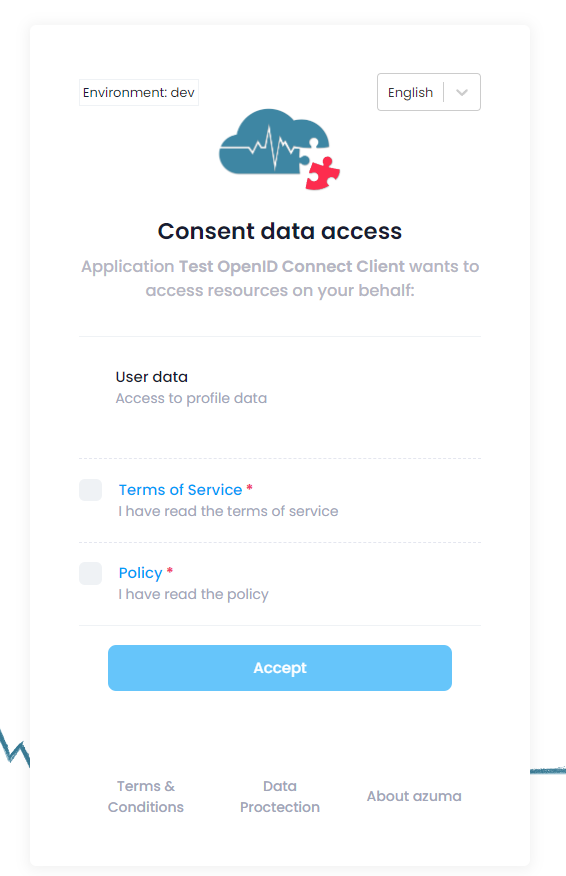
are used in the integrated consent screen.
Example:
Example (client credentials):
The client credentials flow is used for service to service communication. The services can either belong to
- your own product: You authenticate and authorize communication between your own services. Even if your services are not reachable from outside your network environment, this validation provides an extra measure of security.
- to an external product: You authenticate and authorize requests against your API from external sources.
In such cases, it is very important to define the requirements that grant access, such as
scopes. E.g.: thescope"tstapp_data.read"could allow read operations against some data endpoint. While"tstapp_data.write"would also allow modifications of data.
You can create as many clients as needed within your applications in azuma doa.
Example form to create a client:
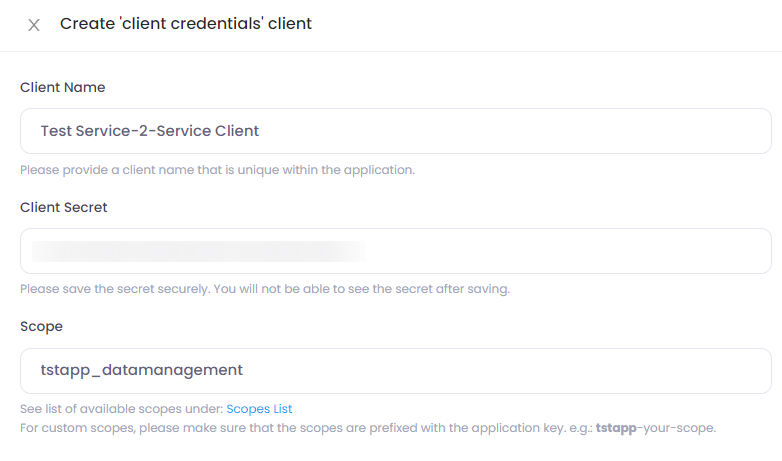
This client allows to request the scope "tstapp_datamanagement".
You can request the access token with that client as follows.
Token url:
Request example:
curl --location --request POST '**token url**' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=client_credentials' \
--data-urlencode 'client_id=**client id**' \
--data-urlencode 'client_secret=**client password**' \
--data-urlencode 'scope=tstapp_datamanagement'
with the following result:
{
"access_token": "...",
"expires_in": 3599,
"scope": "tstapp_datamanagement",
"token_type": "bearer"
}
within the access token, you would find the requested scope:
"scp": [
"tstapp_datamanagement"
]
...